The Heathrow USB
Heathrow investigates after Queen’s security details ‘found on USB drive discovered lying in street’
![]() David Parish – Information Security Consultant
David Parish – Information Security Consultant
There is clearly been a security breach as the above headlines state.
The pen drive found contained 2.5GB of data, including 174 documents, which were not encrypted nor password protected, and some of which were marked ‘confidential’ and ‘restricted’.
The breach obviously causes concerns: hypothetically could have been a copy of the security business continuity or contingency plan for VIP movements at Heathrow.
The question raises the issue – is this a GDPR Data Breach or a Security Breach?
If the data contained no Personal Identifiable Information (PII) it would be a security breach and dealt with internally within the relevant authorities. However, if the USB did contain PII it is a fairly sensitive GDPR Data security breach.
The key issues to consider are, as it is essential as part of your GDPR preparations to consider:
PRESERVING
The Confidentiality
This involves ensuring that information is only accessible to those authorised to access it and therefore to prevent both deliberate and accidental unauthorised access to both information and systems including your network(s), website(s), extranet(s), and e-commerce systems The detailed description of the assets and systems in SCOPE of the ISMS should be detailed in the ISMS Manual of guidance.
The Availability
This means that information and associated assets should be accessible to authorised users when required and therefore physically secure. The Computer network must be resilient and you must be able to detect and respond rapidly to incidents (such as viruses and other malware) that threaten the continued availability of assets, systems and information. There must be appropriate business continuity plans
and Integrity
This involves safeguarding the accuracy and completeness of information and processing methods and therefore requires preventing deliberate or accidental, partial or complete, destruction or unauthorised modification of either physical assets or electronic data. There must be appropriate contingency, data backup plans and security incident reporting. must comply with all relevant data-related legislation in those jurisdictions within which it operates.
of the Physical (assets)
The physical assets including, but not limited to, computer hardware, data cabling, telephone systems, filing systems and physical data files.
and Information Assets
The information assets include information printed or written on paper, transmitted by post or shown in films, or spoken in conversation, as well as information stored electronically on servers, website(s), extranet(s), intranet(s), PCs, laptops, mobile phones and devices, as well as on CD ROMs, floppy disks, USB sticks, backup tapes and any other digital or magnetic media, and information transmitted electronically by any means. In this context, ‘data’ also includes the sets of instructions that tell the system(s) how to manipulate information (i.e. the software: operating systems, applications, utilities, etc.).
The loss of the USB highlights the need to review your
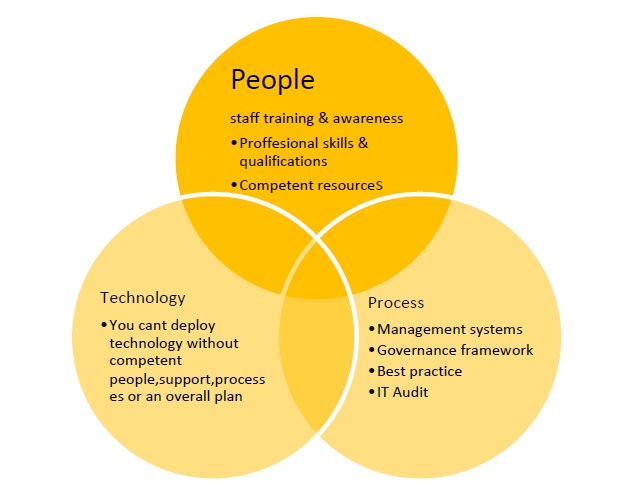
People – some one extracted the data on to a data stick and then lost it.
Process – some one didn’t adhere to a policy or procedure ( if in place if not should be ) on encryption and handling of confidential information.
Technology – The USB wasn’t encrypted the documents weren’t password protected.
All the above issues are requirements of the GDPR.
Top Tips
Protect and keep safe confidential, personal and sensitive information.
Encrypt documents sent out by email or which are shared in a data room or equivalent and which contain confidential, personal or sensitive INFORMATION.
Encrypt USB sticks which contain documents with confidential, personal or sensitive information in them.
Where encryption is necessary, the encryption method must be agreed with the recipient before the documents, USB stick are sent and a suitable “exchange of keys” performed.
Where passwords are used to protect encrypted data, they must be sent separately to the data and only once the recipient’s details have been checked. The strength of the passwords must be in accordance with your Password Policy.
by David Parish, Information Security Consultant – IBITGQ Certified ISO 27001 and GDPR implementation Specialist MSC Security and Risk Management
